Organisational Systems Security
Examples:Potential threats
- Malicious damage: It’s when one or more people intentionally damage your property, which can be inside (internal malicious damage) the organization or outside (external malicious damage). For example, your pc or using malwares. A real life example can be Sony Pictures hack (2014). PlayStation were cyber attacked (external malicious damage) not for the first time. Three years earlier the PlayStation Network saw 77 million users’ personal details compromised. Due to this they had to take their servers down (offline) for 20 days! Now in 2014 the hacker group Guardian of peace brought down Sony’s film division with malware that rendered computers inoperable for two hours, then rebooted them whilst taking all their data. This created a bad image for Sony and affected their economic growth (income). https://www.itpro.co.uk/security/innovation-at-work/29577/the-10-best-or-should-that-be-worst-malware-attacks

- Counterfeit goods: are fakes or unauthorised replicas of the real product which are sold. A real life example is an apple store in China were the sellers were sent fake iPhones by hackers that looked so real. Without the sellers knowing. Later on the police raided them and the workers were confused why they were getting detained by the police. This caused Apple to have a bad image. And had a bad impact on the employers as they were sent to jail and lost their job. This could be seen as piggybacking, as they are using an existing company for their benefits. (internal malicious damage). Fake gaming DVD’s/games were sold by CEX (gaming shop), this from personal experience. https://www.bbc.co.uk/news/technology-14503724#targetText=Now%2C%20according%20to%20Chinese%20trade,visit%20to%20one%20such%20shop.

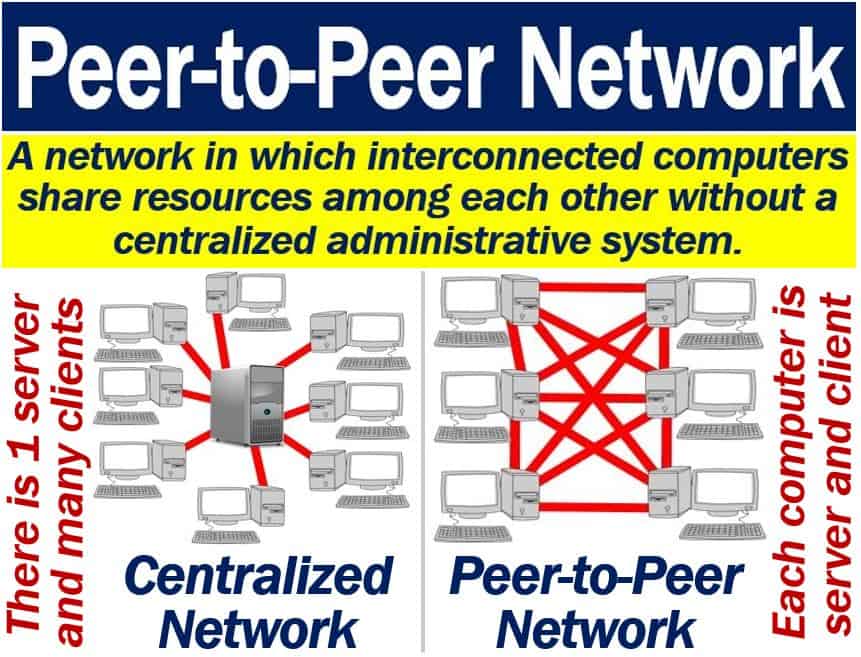
- Peer-to-peer: relating to networks in which each computer can act as a server for the others, allowing shared access to files. Skype is a peer-to-peer example. Because computers share data and information to each other without centralised administrative system. https://en.wikipedia.org/wiki/Peer-to-peer
- Music is an example of counterfeit goods.As there are multiple websites that allows you to download the latest music illegally, as you aren’t paying for it.An example is amoyshare MP3 downloader. This is a personal experience as i use it myself. https://www.amoyshare.com/free-mp3-finder/music-downloader-online.html

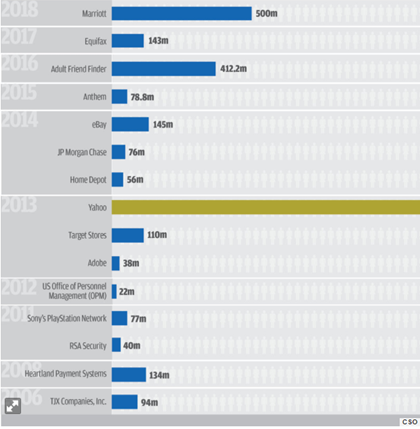
- Technical failures: Equifax which is one of united states largest credit reporting agencies, announced that 143 million of their consumer’s record were stolen by hackers. This occurred in May 2017.This could have been stopped if there was more security put in place, like confidentiality security. For example, 2 step verification or personal questions. This is an example of an external attack. https://techcrunch.com/2018/12/10/equifax-breach-preventable-house-oversight-report/ is when the system doesn’t function properly or as it’s suppose too. This could be a dangerous threat to any organisation as if the system is down or doesn’t function the right way. This will make it easier for the hackers to get into your system leaving you helpless. Therefore, making it harder for you to solve the issue with the technical failure. An example could be the Equifax social security hack. This could be seen as identity theft, because they are using and stealing their personal ID and their identity. Because the bank wouldn’t know who is using his card, if it’s the real owner or the hacker.

- E-commerce: is publicly sharing or advertising your brand on the internet or media. This leads to phishing attacks, money theft, data misuse, credit card frauds and hacking. If there is poor management, or easily fall for free stuff, then this could be a serious threat for your organisation. As you will easily be hacked and all your data/information will be seen and possibly taken. For example, in China there are thousands of pop ups every day. And believe it or not at least 20% of the population that has a device falls for it. https://kotaku.com/in-game-pop-up-scams-chinese-gamer-504362679

- An example of website defacement can be Vogue Magazine UK – Hacked to display dinosaurs wearing fancy hats. This website got hacked and trolled. The hackers changed its visual appearance. https://www.blueshoon.com/the-5-funniest-hacked-website-defacements-ive-ever-seen/

- An example of data via third party suppliers could be eBay or amazon as the sellers will see your address therefore easily find your IP address, and take all your data. An example is a customer (Shahadat Hossain from Barking) who purchased a £280 laptop from amazon and fears that his data got stolen.https://www.thesun.co.uk/money/3362930/im-worried-my-data-was-stolen-in-an-amazon-scam-after-my-purchase-fell-through.

- Denial-of-service attack is when the hacker cyber-attacks a user and stops it from accessing service. The hacker then sends messages and ask for the network. An example could be During the Hong Kong anti-extradition protests in June 2019, the messaging app Telegram was subject to a denial-of-service attack. This was done to prevent protestors from using it to coordinate movements. This made a bad image for telegram.
https://en.wikipedia.org/wiki/Denial-of-service_attack

- Theft of equipement: theft is the taking of another person’s property or service without that person’s permission. An example is an amazon employee was charged with theft of $100,000 in apple watch products. https://www.zdnet.com/article/amazon-employees-charged-with-theft-of-100000-in-apple-watch-products/

- Viruses: A computer virus is a malicious software program loaded onto a user’s computer without the user’s knowledge and performs malicious actions. An example is Honda being shut down due to a virus infecting the computers with a wannacryvirus. https://www.inc.com/will-yakowicz/wannacry-virus-hits-honda-factory-japan.html

- Access without damage:is when hackers access your device, however not doing anything to cause or be a threat.An example is Sage ,where there employees had access to stuff that they should of had.However they didn’t do anything to look as a threat. https://www.observeit.com/blog/5-examples-of-insider-threat-caused-breaches/

- Hacking: a person who uses computers to gain unauthorised access to data.An example of a hacker is Kevin Mitnick. Which is the worlds most known hacker. Once one of the FBI’s Most Wanted because he hacked into 40 major corporations just for the challenge, Kevin is now a trusted security consultant to the Fortune 500 and governments worldwide. https://www.mitnicksecurity.com/about/kevin-mitnick-worlds-most-famous-hacker-biography

- Human error: is when someone accidently did something wrong (mistake). For example, a CS: GO twitch streamer (s1mple) accidently showed his steam password on stream (live). Therefore, in no time getting hacked by a viewer. This allowed the viewer to access his account and steal his expensive items. Later on that day the streamer got his account back as steam client helped him. This minor mistake left him helpless. He could have easily solved this issue by blacking his screen when logging in or by hiding the password. This caused him to lose some expensive items. This is a minor hack as he could have got his identity stolen or his credit details stolen. However, because of this minor error he got more fame from it as it was a funny experience. This minor error could have been easily fixed if he would have used the 2 step verification (information security) which steam has. Or mobile steam management. Which he didn’t use. This is seen as human error. https://techcrunch.com/2019/04/30/twitch-account-hacks/

- Information security: is being protected from hackers who are unauthorised to see or use your information or data. An example could be 2 step verification, or your phone verification (getting a code) and personal questions. An example is that Yahoo in 2013-14 got hacked and 3 billion users account were affected. The attack compromised the real names, email addresses, dates of birth and telephone numbers of 500 million users. This affected their brand name, as well as their image. Therefore, making yahoo’s economical wealth decrease.This is an example of data integrity and confidentiality. https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html
- Organisational impact: are customers impact on business units or departments. This is used to connect the customer experience to business. An example could be Microsoft which was struggling to write its second act. The well-known company was struggling and fighting with other major business units. They were at war (very competitive). One of them is google.https://www.tinypulse.com/blog/3-examples-of-organizational-change-and-why-they-got-it-right

- Loss of service/business/income is the loss of electrical power, to one or more customers. An example could be Microsoft side kick. In 2009, the Microsoft Sidekick servers experienced failure, and lost tons of customer data including contacts, calendar appointments, and to do lists. They never had any sort of back up for their files. Therefore, all the data was forever lost. They have learnt from their experience. However, this affected their brand name, there was less sells. Therefore Microsoft has a poor image.

- Loss of income refers to the situation in which a person’s source of money for expenses, such as his salary is terminated. For example, uber lost 5.2 billion dollars in 3 months!

- Information Security (data integrity/confidentiality): An example is bank account statements and credit card numbers. Data integrity is the maintenance of, and the assurance of the accuracy and consistency of. An example is Equifax (2013-14) being hacked and hundreds of people’s information and data was taken by hackers. As there security was poor. https://techcrunch.com/2018/12/10/equifax-breach-preventable-house-oversight-report/
